Attack & attackers description :
The Equation Group is a highly advanced and secretive cyber espionage collective believed to be affiliated with a nation-state, with strong evidence pointing to the United States. Active since at least 2001, the Equation Group has gained notoriety for its sophisticated cyber attack capabilities and highly targeted operations. This technical article delves into the advanced techniques and notable activities associated with the Equation Group, shedding light on their advanced malware, surveillance tools, and the implications for cybersecurity.
Advanced Techniques and Operations:
- Exploitation of Zero-Day Vulnerabilities: The Equation Group is renowned for its ability to exploit zero-day vulnerabilities, leveraging undisclosed software flaws to infiltrate target systems. By discovering and exploiting these vulnerabilities, the group can gain initial access to targeted networks with minimal detection.
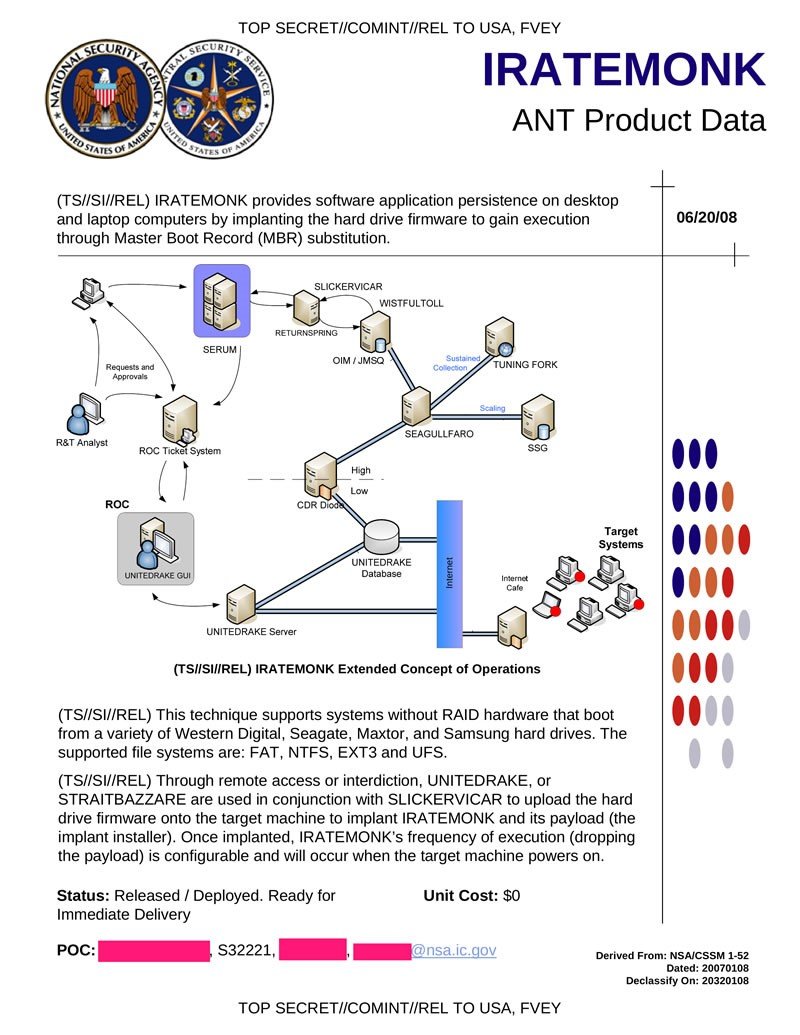
- Advanced Malware: The Equation Group has developed and employed a range of advanced malware tools to conduct its operations. Among the notable malware associated with the group are EquationDrug, EquationLaser, EquationMist, and GrayFish. These sophisticated malware strains enable deep surveillance, data exfiltration, and remote control of compromised systems.
- Stuxnet: The Equation Group is believed to have played a role in the development of the infamous Stuxnet worm, which targeted Iran’s nuclear facilities in 2010. Stuxnet showcased the group’s ability to design and execute highly targeted cyber attacks on critical infrastructure, highlighting their expertise in cyber warfare.
- Persistent Implant Techniques: The Equation Group utilizes persistent implant techniques to maintain a long-term presence within compromised systems. These techniques involve stealthy mechanisms for persistence, such as BIOS and firmware implants, ensuring continued access and control even after system reboots or software updates.
Impact of Notable Activities:
- Targeting Nation-States: The Equation Group has primarily focused its operations on nation-states, with a particular interest in geopolitical adversaries. Their targets have included governments, military organizations, and critical infrastructure sectors, aiming to gather intelligence and gain an advantage in strategic affairs.
- International Espionage: The group has engaged in extensive international espionage, targeting diplomatic missions, embassies, and foreign government entities. Their operations have involved sophisticated surveillance techniques and data exfiltration to obtain sensitive diplomatic, political, and economic information.
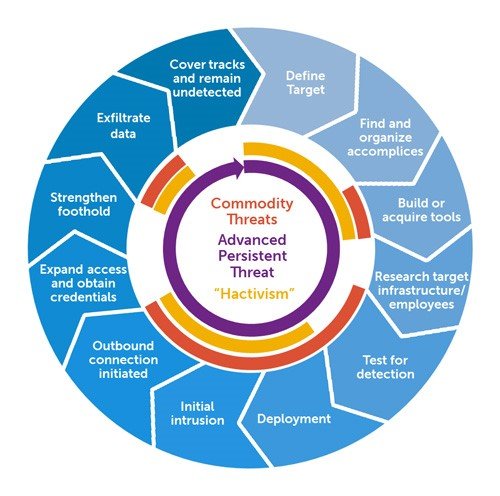
- Advanced Persistent Threat Operations: The Equation Group’s operations follow advanced persistent threat (APT) tactics, with a strong emphasis on stealth, persistence, and long-term intelligence gathering. They exhibit a deep understanding of their targets’ infrastructure and utilize tailored attack vectors to maximize their success.
Mitigations : The Equation Group’s activities highlight significant implications for global cybersecurity:
- Robust Vulnerability Management: Given the group’s proficiency in exploiting zero-day vulnerabilities, organizations must prioritize timely patching and vulnerability management to minimize the risk of being targeted.
- Enhanced Detection and Response Capabilities: Deploying advanced threat detection and response systems, such as intrusion detection systems (IDS), security information and event management (SIEM) solutions, and endpoint detection and response (EDR) tools, can aid in detecting and responding to the Equation Group’s sophisticated attacks.
- Supply Chain Security: Organizations should adopt robust supply chain security practices to mitigate the risk of compromise through tampered hardware, software, or firmware. Thorough vetting and monitoring of vendors, along with strong integrity checks, are essential in preventing potential backdoors or malicious implants.
- Intelligence Sharing and Collaboration: Cooperation between cybersecurity organizations, government agencies, and international entities is crucial in sharing threat intelligence and identifying the group’s evolving tactics. Timely information sharing can contribute to proactive defense strategies and the development of effective countermeasures.
Take away: The Equation Group’s advanced capabilities and long-standing presence in the cyber espionage landscape make them a formidable threat. Understanding their techniques, malware arsenal, and targeted operations is essential for organizations and governments to enhance their cybersecurity posture. By implementing robust security measures, prioritizing vulnerability management, and fostering collaborative information sharing, entities can better defend against the Equation Group’s sophisticated cyber attacks and protect critical infrastructure and sensitive information.
Disclaimer : The information provided herein is on “as is” basis, without warranty of any kind.