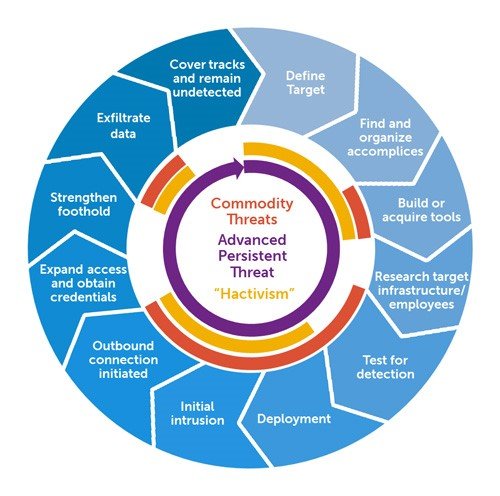
Attack & attackers description :DarkHotel is an advanced persistent threat (APT) group that has been active since 2007, targeting high-profile individuals such as business executives, government officials, and diplomats. Operating with a high level of sophistication and discretion, DarkHotel employs a combination of social engineering, zero-day exploits, and advanced malware to compromise its targets. This technical article delves into the tactics, techniques, and impact of the DarkHotel APT, shedding light on the persistent nature of this cyber threat.
Attack Methodologies:
- Watering Hole Attacks: DarkHotel often utilizes watering hole attacks, infecting legitimate websites commonly visited by its targets. By compromising these sites and injecting malicious code, the group can silently deliver malware to visitors’ devices, exploiting vulnerabilities in browsers or other software.
- Spear Phishing: DarkHotel employs highly targeted spear phishing campaigns tailored to specific individuals. These emails appear genuine and often contain malicious attachments or links that, when clicked, initiate the infection process. The group conducts extensive research on its targets to craft convincing messages and increase the likelihood of successful compromise.
- Advanced Malware: DarkHotel employs sophisticated malware, including custom-designed backdoors and keyloggers, to gain persistent access to compromised systems. The group continually evolves its malware arsenal, utilizing zero-day exploits and leveraging encryption and anti-detection techniques to evade traditional security measures.
- Social Engineering: DarkHotel excels in social engineering tactics, exploiting human vulnerabilities to gain access to sensitive information. This can involve impersonating hotel staff, creating fake Wi-Fi networks, or manipulating hotel reservation systems to trick targets into connecting to malicious networks or disclosing credentials.
Impact :
- Corporate Espionage: DarkHotel primarily targets individuals associated with multinational corporations and government organizations. By compromising executives and key personnel, the group aims to gather sensitive business information, trade secrets, and intellectual property, facilitating corporate espionage and giving its own clients a competitive advantage.
- Diplomatic and Government Networks: DarkHotel has also targeted government officials and diplomats, with a particular focus on Asian countries. By infiltrating their systems, the group gains access to classified information, confidential communications, and insights into diplomatic negotiations, enabling potential political leverage or intelligence gathering.
- Persistent Surveillance: DarkHotel maintains long-term access to compromised systems, allowing continuous surveillance of targeted individuals. This capability provides the group with an ongoing stream of sensitive information, which can be exploited for multiple purposes, including future attacks or blackmail.
Mitigation :
- User Awareness and Training: Educating high-profile individuals and employees about the risks associated with spear phishing and social engineering is crucial. Regular training programs can help individuals recognize and report suspicious emails or activities, reducing the chances of successful compromise.
- Vulnerability Management: Timely patching of software and systems is essential to mitigate the risk of zero-day exploits. Organizations should have robust vulnerability management processes in place to identify and address potential weaknesses promptly.
- Multi-Factor Authentication (MFA): Implementing MFA across all systems and accounts adds an extra layer of security, making it harder for attackers to gain unauthorized access even if credentials are compromised.
- Network Segmentation and Monitoring: Employing network segmentation isolates critical systems from the rest of the network, limiting the potential lateral movement of attackers. Continuous monitoring of network traffic and endpoint activities helps detect and respond to any indicators of compromise.
Take away: DarkHotel’s long-standing presence and persistent targeting of high-profile individuals highlight the need for heightened cybersecurity measures and user vigilance. By adopting a multi-layered security approach, including user training, vulnerability management, and proactive monitoring, organizations can better defend against this sophisticated APT. Additionally, collaboration between governments, intelligence agencies, and private-sector
Disclaimer : The information provided herein is on “as is” basis, without warranty of any kind.