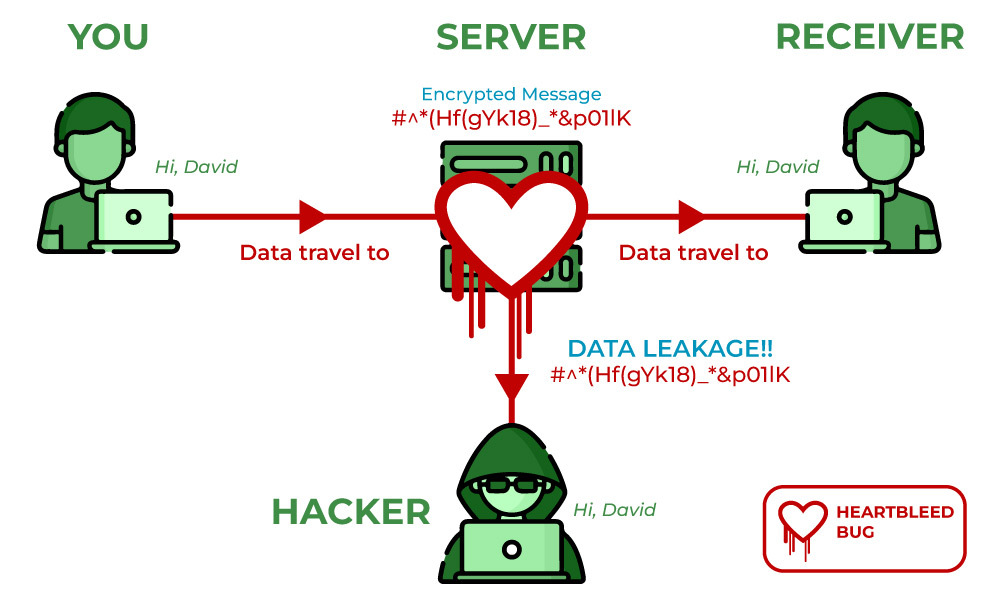
Attack description : The Heartbleed vulnerability, discovered in 2014, sent shockwaves through the cybersecurity community, exposing a critical flaw in the OpenSSL cryptographic library. In this technical article, we delve into the intricacies of the Heartbleed vulnerability, dissecting its underlying causes, the mechanics of the exploit, and its potential impact on security.
The Heartbleed vulnerability was a result of a programming error within the OpenSSL library, specifically in the implementation of the Transport Layer Security (TLS) protocol’s heartbeat extension. At its core, the vulnerability allowed an attacker to exploit a buffer over-read bug, potentially exposing fragments of sensitive data residing in the memory of vulnerable systems.
Exploitation Mechanics: To fully comprehend the technical aspects of the Heartbleed vulnerability, consider the following key points:
- Heartbeat Protocol: The TLS heartbeat extension enables a client and server to exchange small, arbitrary blocks of data to maintain an active connection. This involves the transmission of a payload and the corresponding payload length.
- Buffer Over-read Bug: Within OpenSSL’s heartbeat implementation, a critical flaw existed in the bounds checking of the payload length. An attacker could craft a malicious heartbeat request, providing an inflated payload length value that exceeded the actual length of the payload.
- Memory Exposure: By sending the malicious heartbeat request to a vulnerable server, the attacker could trick the server into leaking fragments of its memory contents. The response from the server would include the requested payload length number of bytes, inadvertently disclosing data stored in memory, potentially including sensitive information.
Impact: The Heartbleed vulnerability had far-reaching implications, primarily due to its potential to expose sensitive data from the server’s memory:
- Private Keys: One of the most critical risks associated with Heartbleed was the potential exposure of private keys used for SSL/TLS certificates. Compromised private keys could allow attackers to decrypt encrypted communications or impersonate the affected server.
- User Credentials: Heartbleed could also expose usernames, passwords, and session cookies stored in the memory of vulnerable servers. This information could be leveraged by attackers to gain unauthorized access to user accounts or perform further malicious activities.
- Application Data: Beyond credentials, the vulnerability had the potential to expose fragments of application-specific data residing in memory. This could include database contents, personally identifiable information (PII), or any other data processed by the vulnerable application.
Mitigation : In response to the Heartbleed vulnerability, several key actions were taken to mitigate its impact and prevent further exploitation:
- Security Patch Deployment: The OpenSSL project promptly released a security patch addressing the vulnerability. System administrators and service providers were advised to apply the patch immediately to protect their systems from exploitation.
- Certificate Revocation and Replacement: Organizations utilizing affected versions of OpenSSL were advised to revoke and replace their SSL/TLS certificates to mitigate the risk of compromised private keys.
- User Notification and Password Resets: Service providers and website operators promptly notified their users about the vulnerability, advising them to change their passwords as a precautionary measure against potential credential exposure.
- Network Monitoring and Intrusion Detection: Intrusion detection systems and network monitoring tools were updated to detect potential exploitation attempts targeting the Heartbleed vulnerability. Network traffic analysis and anomaly detection played a crucial role in identifying suspicious activity.
Take away: The Heartbleed vulnerability of 2014 exposed a critical security flaw in the OpenSSL library, highlighting the importance of thorough code review, patch management, and secure programming practices. By understanding the technical intricacies of the vulnerability and its potential impact, organizations can strengthen their security defenses and take proactive measures to safeguard against similar vulnerabilities in the future.
Disclaimer : The information provided herein is on “as is” basis, without warranty of any kind.