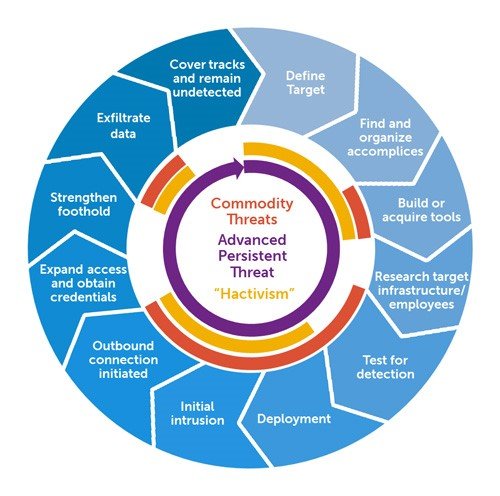
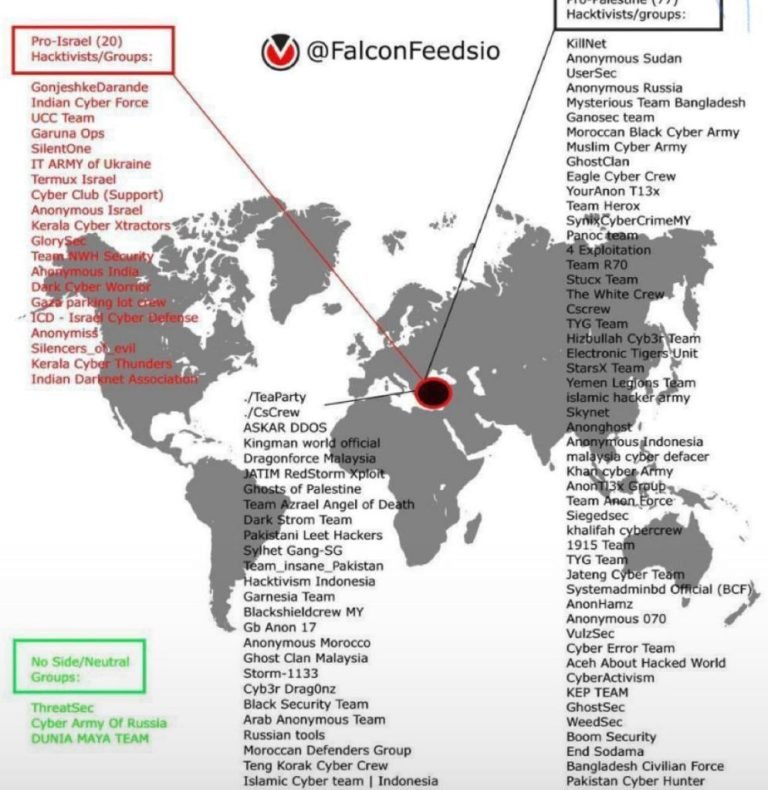
Attack Description :
On their leak site, the CL0P ransomware group asserted that they have targeted nine additional victim organizations. However, as of now, no sample data has been made public to validate their assertions. The affected organizations include American Airlines, Jonas Fitness Inc, SMC³ Inc, ITT Inc, Bluefin Payment Systems LLC, Ventiv Technology, and Data Media Associates LLC, all of which are based in the United States.
Impact of the Ransomeware:
- Data Encryption and Loss: Ransomware encrypts critical data, rendering it inaccessible to the organization until a ransom is paid. This could result in data loss if proper backups are not in place.
- Operational Disruptions: The attack can disrupt regular business operations, leading to downtime, decreased productivity, and potential financial losses.
- Financial Impact: Organizations may face financial losses due to ransom payments, recovery costs, and potential legal and regulatory consequences.
- Reputational Damage: Publicly disclosed ransomware attacks can harm an organization’s reputation, eroding customer trust and investor confidence.
- Legal and Regulatory Ramifications: The attack could lead to legal actions, regulatory investigations, and compliance issues related to data protection and cybersecurity.
- Intellectual Property Theft: Ransomware attackers may exfiltrate sensitive intellectual property, compromising the organization’s competitive advantage.
- Customer and Employee Concerns: Customers and employees may be concerned about the security of their personal information and may lose confidence in the organization’s ability to protect their data.
Mitigation Strategies:
While no security measure can provide absolute protection against ransomware attacks, organizations can adopt several strategies to mitigate the risks and minimize the impact:
- Data Backups: Regularly back up critical data to offline or secure systems. This enables organizations to restore their data without paying a ransom.
- Network Segmentation: Segment the network to limit the spread of ransomware, reducing the potential impact of an infection.
- Security Awareness Training: Educate employees about phishing attacks and other social engineering techniques to prevent the inadvertent activation of ransomware.
- Patch Management: Keep all software and systems up to date with the latest security patches to address known vulnerabilities.
- Access Control: Limit user access privileges to only what is necessary for their roles, reducing the potential damage if an account is compromised.
- Antivirus and Endpoint Protection: Deploy robust antivirus and endpoint protection solutions to detect and block ransomware.
- Incident Response Plan: Develop and regularly test an incident response plan that outlines the steps to take in the event of a ransomware attack.
- Encryption and Multi-Factor Authentication: Encrypt sensitive data and enforce multi-factor authentication to enhance security.
- Regular Security Audits: Conduct regular security assessments and penetration testing to identify and address vulnerabilities.
- Cyber Insurance: Consider acquiring cyber insurance to help cover the costs associated with ransomware attacks and data breaches.
Take Away: No security measure can provide absolute protection against ransomware attacks but Implementing a comprehensive cybersecurity strategy, combined with proactive measures, can enhance an organization’s resilience to ransomware attacks and better protect sensitive data and systems. Disclaimer : The information provided herein is on “as is” basis, without warranty of any kind.