Attack & attackers description : Operation Olympic Games, conducted between 2006 and 2010, was a highly classified and covert cyber warfare campaign jointly conducted by the United States and Israel. This operation targeted Iran’s nuclear facilities, aiming to disrupt and delay its nuclear weapons development program. This technical article delves into the intricacies of Operation Olympic Games, including the attack methodologies, the Stuxnet worm, and the implications for cyber warfare and international security.
Attack Methodologies:
- Stuxnet Worm: Operation Olympic Games leveraged the Stuxnet worm, one of the most sophisticated and complex pieces of malware ever discovered. Stuxnet targeted supervisory control and data acquisition (SCADA) systems, specifically those used in Iran’s nuclear infrastructure. The worm employed multiple zero-day vulnerabilities and utilized various propagation methods, including infected USB drives and network vulnerabilities, to infiltrate the target systems.
- PLC Exploitation: Stuxnet specifically targeted Programmable Logic Controllers (PLCs) used in centrifuge control systems. It manipulated the code within the PLCs, causing them to malfunction and sabotage the uranium enrichment process. This attack methodology demonstrated a deep understanding of the target infrastructure and the ability to compromise critical control systems.
- Covert Operations: Operation Olympic Games relied on covert operations to gain physical access to the target facilities and deploy the Stuxnet malware. This involved intelligence gathering, social engineering, and the exploitation of insiders or supply chain vulnerabilities. The combination of cyber and physical elements made the operation highly sophisticated and difficult to detect.
Impact of Cyber Warfare:
- Escalation of Cyber Warfare: Operation Olympic Games marked a significant milestone in the evolution of cyber warfare, showcasing the potential for targeted attacks on critical infrastructure. It blurred the lines between traditional warfare and cyber operations, demonstrating the ability to cause physical damage and disruption through cyberspace.
- International Norms and Regulations: The operation raised questions about the development of international norms and regulations regarding cyber warfare. The use of offensive cyber capabilities against another nation’s critical infrastructure challenged traditional rules of engagement and highlighted the need for diplomatic discussions on the boundaries and consequences of such actions.
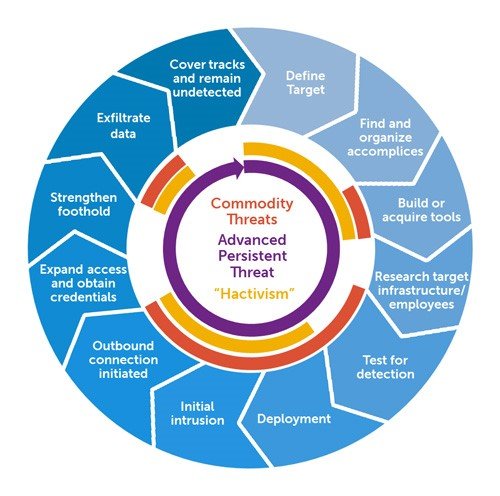
- Advanced Persistent Threats (APTs): Operation Olympic Games highlighted the capabilities of advanced persistent threats, showing that state-sponsored actors can invest significant resources and expertise into conducting long-term cyber operations. It emphasized the importance of proactive defense measures and the need for robust cybersecurity strategies to defend against such persistent threats.
Mitigations :
- Attribution Challenges: Operation Olympic Games revealed the difficulties in attributing cyber attacks to specific actors. The operation was highly covert, involving multiple nations and complex attack methodologies, making it challenging to definitively attribute responsibility. This underscores the need for robust investigative capabilities and international cooperation in cyber incident response.
- Critical Infrastructure Protection: The operation underscored the vulnerability of critical infrastructure to cyber attacks. It emphasized the need for enhanced security measures, including network segmentation, intrusion detection systems, and strict access controls, to protect critical systems and minimize the potential for physical harm or disruption.
- Defense-in-Depth Strategies: Operation Olympic Games highlighted the importance of defense-in-depth strategies that encompass multiple layers of security controls. This includes continuous monitoring, timely patching, strong access controls, and proactive threat hunting to detect and mitigate advanced cyber threats targeting critical infrastructure.
Take away:
Operation Olympic Games marked a watershed moment in the realm of cyber warfare, demonstrating the potential for cyber attacks to disrupt and damage critical infrastructure. The deployment of the Stuxnet worm against Iran’s nuclear facilities showcased the convergence of cyber and physical elements in offensive operations. It emphasized the need for international dialogue on the norms and regulations surrounding cyber warfare and the importance of robust cybersecurity measures to defend against advanced persistent threats. Operation Olympic Games serves as a reminder of the evolving threat landscape and the critical role of cybersecurity in safeguarding national security and global stability.
Disclaimer : The information provided herein is on “as is” basis, without warranty of any kind.