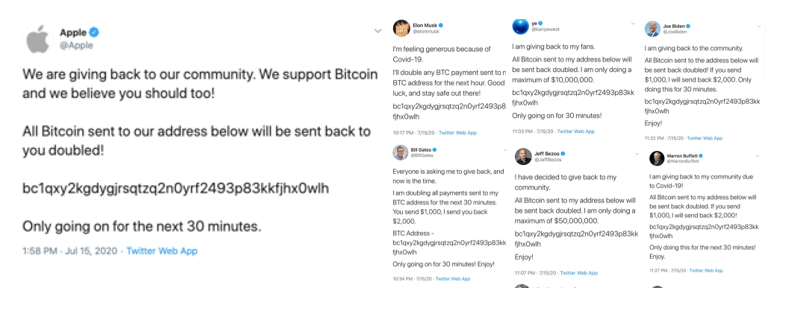
Attack description : The Twitter Bitcoin scam attack of 2020 shook the online community, highlighting the vulnerabilities of social media platforms and the potential for large-scale fraud. This technical article delves into the details of the attack, exploring the social engineering tactics employed, the impact on Twitter’s security, and the implications for online trust and user authentication.
The Twitter Bitcoin scam attack involved a coordinated effort by attackers to compromise high-profile Twitter accounts and deceive followers into sending cryptocurrency payments. The following technical aspects played a role in the success of the attack:
- Spear Phishing: The attackers employed sophisticated spear phishing techniques to gain unauthorized access to Twitter’s internal tools. By targeting a small group of Twitter employees through convincing emails or messages, the attackers tricked them into revealing their account credentials or granting access to sensitive systems.
- Account Takeover: Once inside Twitter’s infrastructure, the attackers seized control of prominent accounts, including those of verified celebrities, politicians, and influential personalities. This enabled them to post fraudulent messages, luring followers into sending Bitcoin payments to the attacker-controlled wallets.
Impact : The Twitter Bitcoin scam attack had significant ramifications, shedding light on the risks associated with social media platforms and the potential erosion of online trust:
- Financial Losses: Numerous Twitter users fell victim to the scam, resulting in substantial financial losses as they sent cryptocurrency payments to the fraudulent addresses. This highlighted the urgent need for user education and skepticism towards unsolicited online requests for money.
- Reputation Damage: The incident tarnished Twitter’s reputation as a trusted platform. The compromise of high-profile accounts undermined the credibility of the platform’s security measures, leading to a loss of user confidence and a dent in Twitter’s brand image.
- Heightened Concerns over Data Privacy: The breach emphasized the importance of protecting user data on social media platforms. With access to internal tools, the attackers had potential access to users’ private messages and other sensitive information. This raised concerns about data privacy and the adequacy of security measures implemented by social media platforms.
Enhancing Security and Trust in Online Platforms: The Twitter Bitcoin scam attack served as a catalyst for reinforcing security practices and user authentication methods:
- Multi-Factor Authentication (MFA): Implementing MFA for user accounts adds an extra layer of protection, making it more difficult for attackers to gain unauthorized access, even if they obtain account credentials.
- Employee Security Awareness: Organizations should prioritize comprehensive training programs to educate employees about social engineering tactics, phishing threats, and the importance of securely handling user data. This helps mitigate the risk of insider attacks and improves overall security posture.
- Incident Response and Communication: Swift and transparent communication during security incidents is crucial to mitigate the impact and maintain trust. Organizations must have incident response plans in place to promptly address breaches, protect affected users, and communicate updates and actions taken to restore security.
- User Education and Vigilance: Raising awareness among users about potential scams, phishing attempts, and fraudulent schemes helps foster a vigilant and skeptical online community. Educating users on secure online practices and promoting skepticism towards unsolicited requests for personal information or financial transactions can help prevent similar attacks.
Take away: The Twitter Bitcoin scam attack of 2020 serves as a stark reminder of the evolving tactics employed by cybercriminals to exploit social media platforms for financial gain. By implementing robust security measures, prioritizing employee training, and promoting user education, online platforms can enhance their defenses against social engineering attacks and safeguard the trust and security of their users.
Disclaimer : The information provided herein is on “as is” basis, without warranty of any kind.